Step-up authentication
You can set up multi-factor authentication to work in one of two models:
- Strict, where secured operations always require the highest Authenticator Assurance Level (AAL).
- Lax, where the secured operations require only the
aal1Authenticator Assurance Level (AAL).
You can set the required authentication model for these operations/endpoints:
- User sign-in (getting an Ory Session) /
/sessions/whoamiendpoint - Self-service user settings
In the Ory Network, the default multi-factor authentication enforcement model is Strict. This means that high-risk operations such as updating user settings require step-up authentication by default.
Configuration
- Ory Console
- Ory CLI
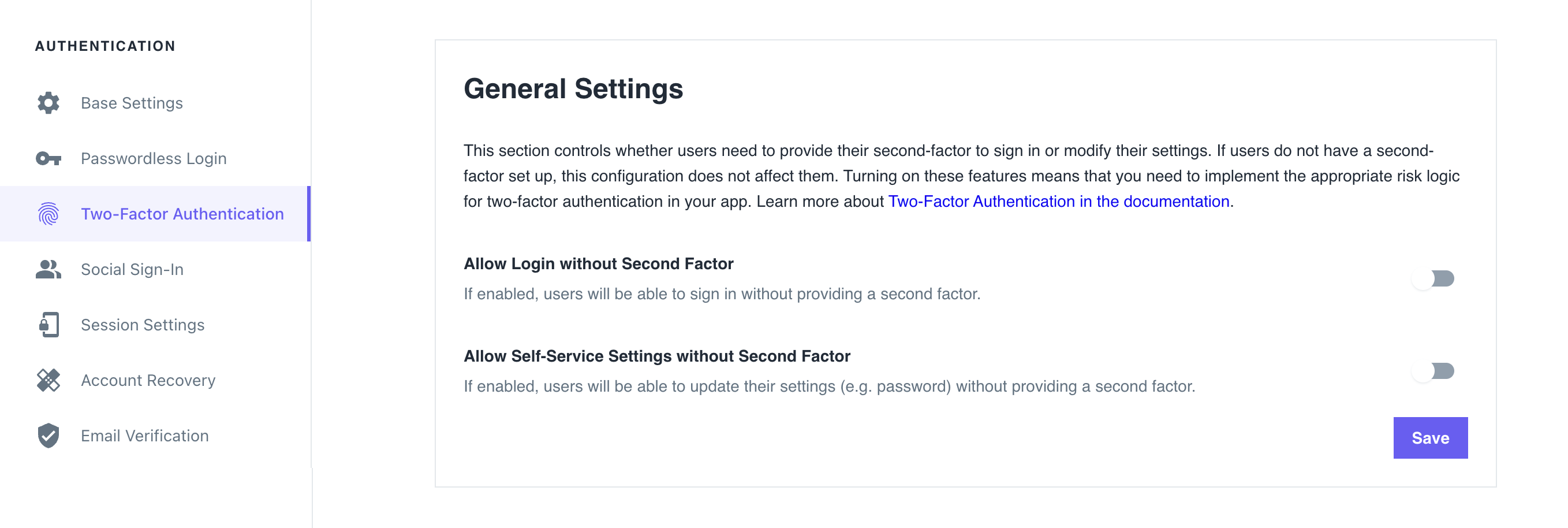
To change the multi-factor authentication enforcement to Lax and allow users to sign in or access user settings without authenticating with the second factor, go to the Ory Console → Two-Factor Authentication and use the switches in the General Settings section.
Follow these steps to adjust the settings in the Ory Network using the Ory CLI:
Get the Ory Identities configuration from your project and save it to a file:
## List all available projects
ory list projects
## Get config
ory get identity-config {project-id} --format yaml > identity-config.yamlAdjust the values of the indicated keys to the desired values:
identity-config.yaml# ...
selfservice:
flows:
settings:
required_aal: highest_available
# ...
session:
whoami:
required_aal: highest_available
# ...tipUse
aal1for the Lax model andhighest_availablefor the Strict model. The default value in Ory Network ishighest_available.Update the Ory Identities configuration using the file you worked with:
ory update identity-config {project-id} --file identity-config.yaml
Trigger step-up authentication
You can make users complete a second authentication factor in their current session by initiating a new login flow using one of
these endpoints with the aal parameter set to aal2:
For example:
/self-service/login/browser?aal=aal2
/self-service/login/api?aal=aal2
If the Ory Session has aal2 already, this will error. In that case, you can request to refresh the session using the second
factor:
/self-service/login/browser?refresh=true&aal=aal2
/self-service/login/api?refresh=true&aal=aal2
When the user successfully provides their configured second factor:
- The method, for example
totp, is added to the Ory Session. - Ory Session Authenticator Assurance Level (AAL) is set to
aal2. - The
authenticated_attime is set to the time when the user provides the second factor.